Phishing attacks are those in which unsuspecting users are lured to a rogue website that mimics a legitimate website and are fooled into giving up their login credentials or other sensitive information to the rogue site. It has been a serious threat against ordinary users on the Internet. Current solutions for steering users away from phishing websites are typically server-based and have several drawbacks. They impact user privacy and are not effective against attackers who can adaptively serve different content to different clients. Moreover, while they might warn a user about a phishing website, they offer no guidance as to how the user can find the real website that they intended to go to in the first place.
To address these limitations, we have developed Off the hook, a phishing website protection add-on. Off the hook is implemented entirely on client-side. Consequently, it is privacy-preserving and is able to detect adaptive attacks. It is very efficient and fast at detecting phishing websites. It can also identify the target of a phishing website . The add-on displays warning messages in real-time as a user is browsing the Web.
Challenges in Phishing Detection: Phishing websites do not exploit any technical flaw but take advantage of the inability of ordinary users to effectively link a physical identity (e.g. a person, a company) to an electronic identity (e.g. a website, an email). Phishers mostly use social engineering techniques to impersonate an identity to lure their victims. Given their non-technical nature, protecting against phishing attacks is challenging. In addition, phishers use tricks such as serving different content (legitimate/phishing) to different client requests in order to defeat current centralized detection systems that crawl the Web from a single location. Blacklists of URLs are built based on this centralized analysis; when a user visits a webpage, it is checked against these lists to warn the user about phishing websites. This requires users to effectively disclose their entire browsing history to the centralized anti-phishing services, thus raising a serious privacy concern.
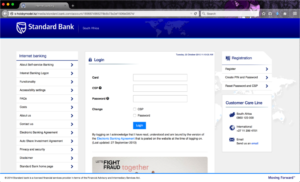 |
| An example phishing page |
Control and Constraints: A phisher mimics the look and feel of a target website. However, he does not have complete freedom in doing so. Some attributes of a webpage (displayed in a browser) are beyond the control of the phisher while others impose certain constraints on him. We modeled these aspects of control and constraints in the features we chose for Off the hook, our machine learning based detection system. By assessing the consistency of the information contained in controlled/uncontrolled and constrained/unconstrained elements of a webpage, Off the hook is able to identify phishing websites and their targets effectively. Off the hook outperforms several state-of-the-art methods in terms of accuracy and speed while distinguishing itself in its privacy-friendliness and its resilience to adaptive attacks. In addition, the identification of phishing webpage relies solely on the data extracted from the webpage and no external source of information which makes it language- and brand-independent and admit a client-side-only implementation.
Add-on: Off the hook is implemented as a browser add-on that analyses visited webpages in real-time. If a webpage is identified as phishing, interaction with the website is disabled and an interstitial warning message pops up in less than half a second. The user is then presented with several choices including the option of being redirected to the identified likely target, getting back to a search engine or proceeding to the website with the option to whitelist it. The user interface has been refined using a cognitive walkthrough exercise in order to provide intelligible and efficient warnings to protect unsavvy users.
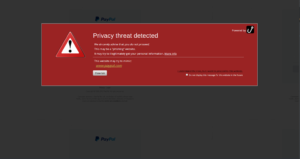 |
| Interstitial warning page from Off the hook |
Off the hook add-on is available for Mozilla Firefox and Google Chrome, and supported on Windows, Mac OS X and Ubuntu. Download and installation instructions are available in our project page.
More detailed information about the phishing detection and target identification methodology can be found in our ICDCS paper and our technical report. Implementation details for the add-on and phishing warnings are available in our ICDCS demo paper.
This work is supported by the Academy of Finland (via the Contextual Security project) and the Intel Collaborative Research Institute for Secure Computing.
