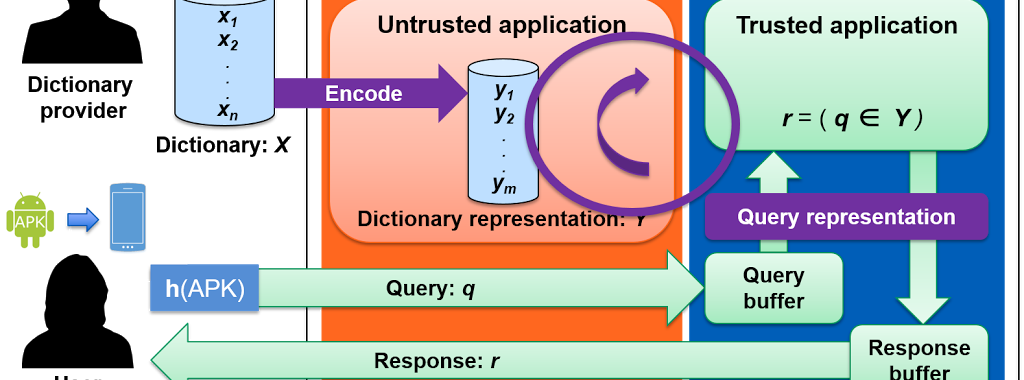
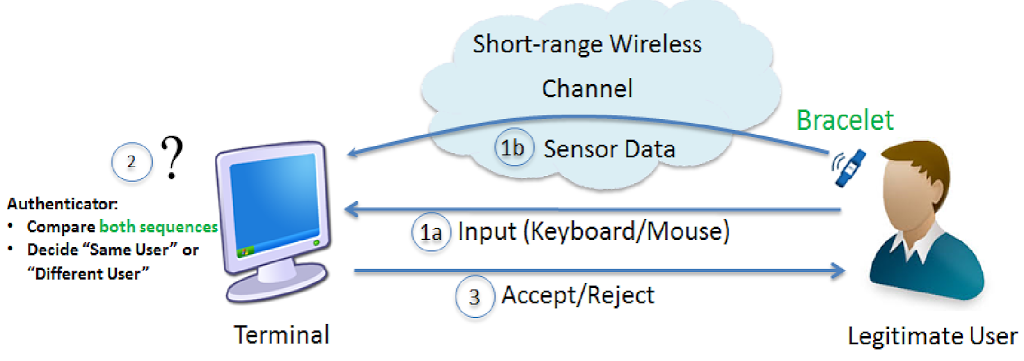
Common sense applications of trusted hardware
Hardware security mechanisms like ARM TrustZone and Intel SGX have been widely available for a while and the academic research community is finally paying attention. Whether these mechanisms are safe and useful for ordinary people is hotly debated. In this post, we sketch two of our “common sense” applications of hardware-based trusted execution environments. Hardware […]